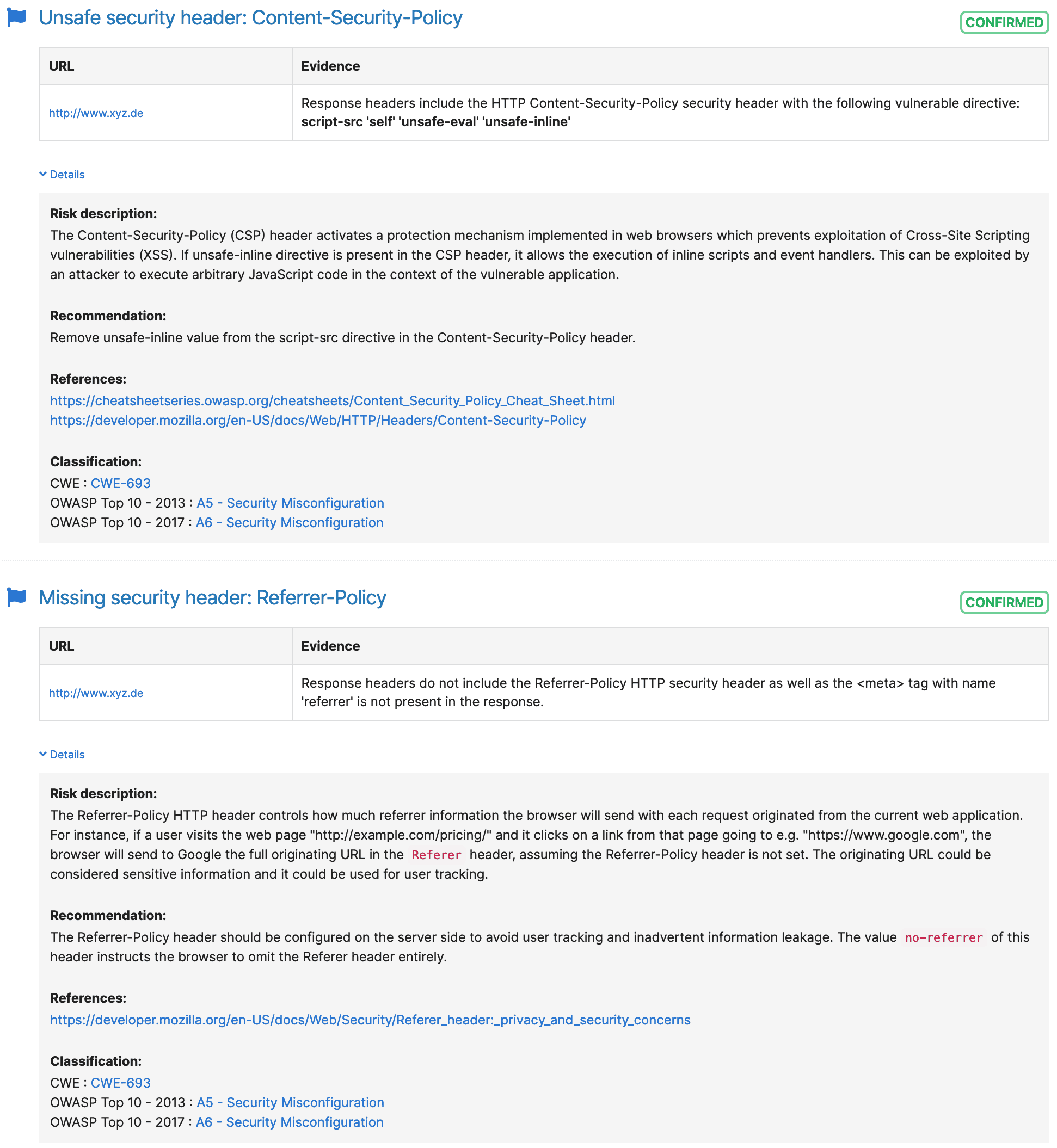
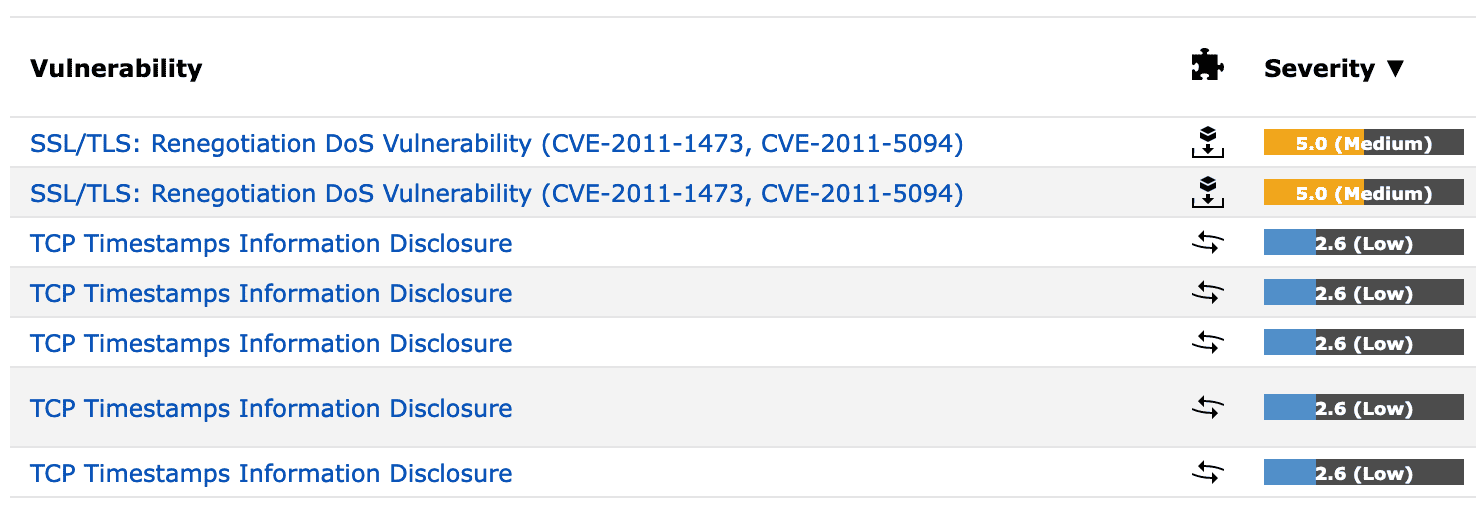
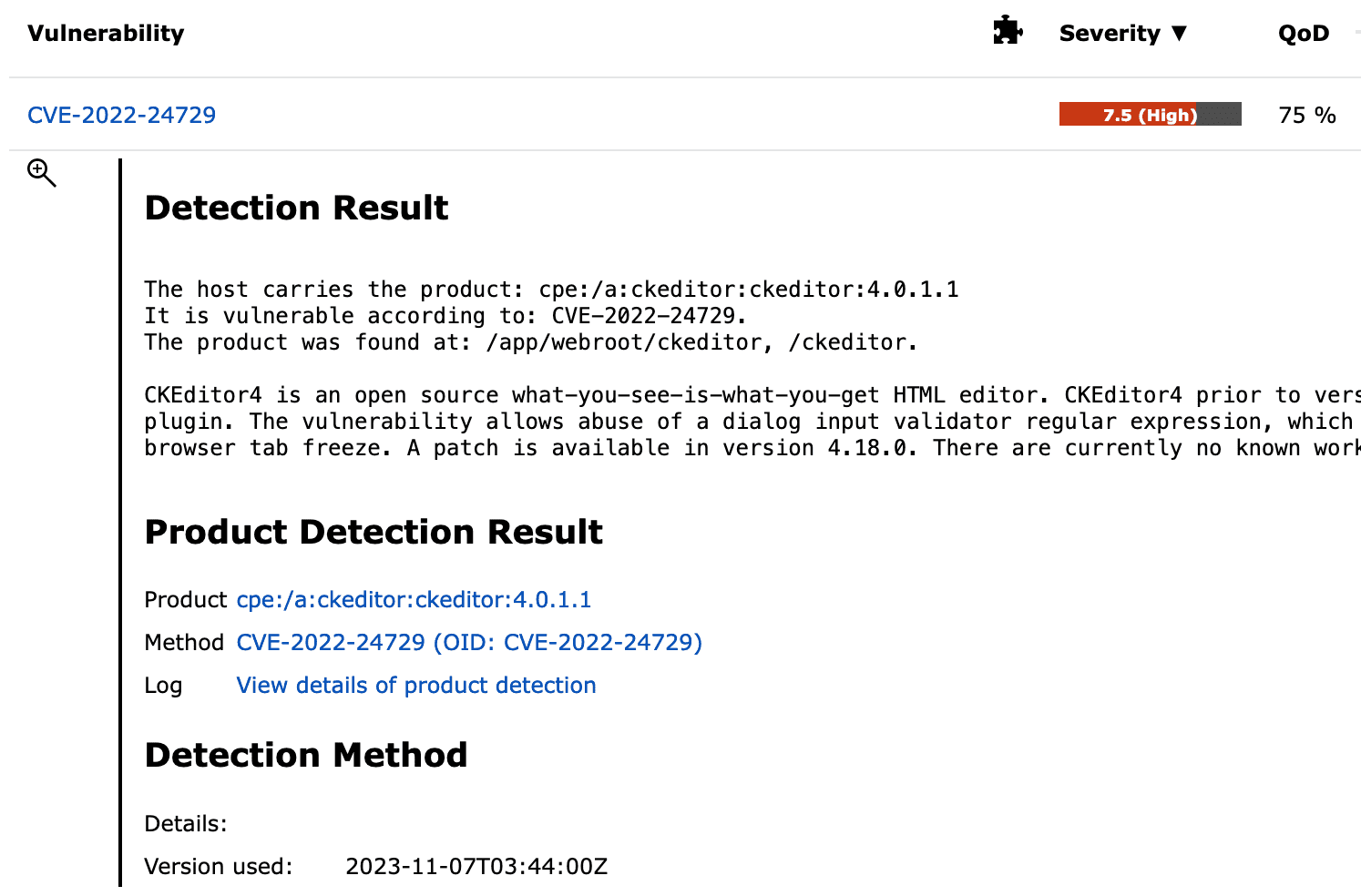
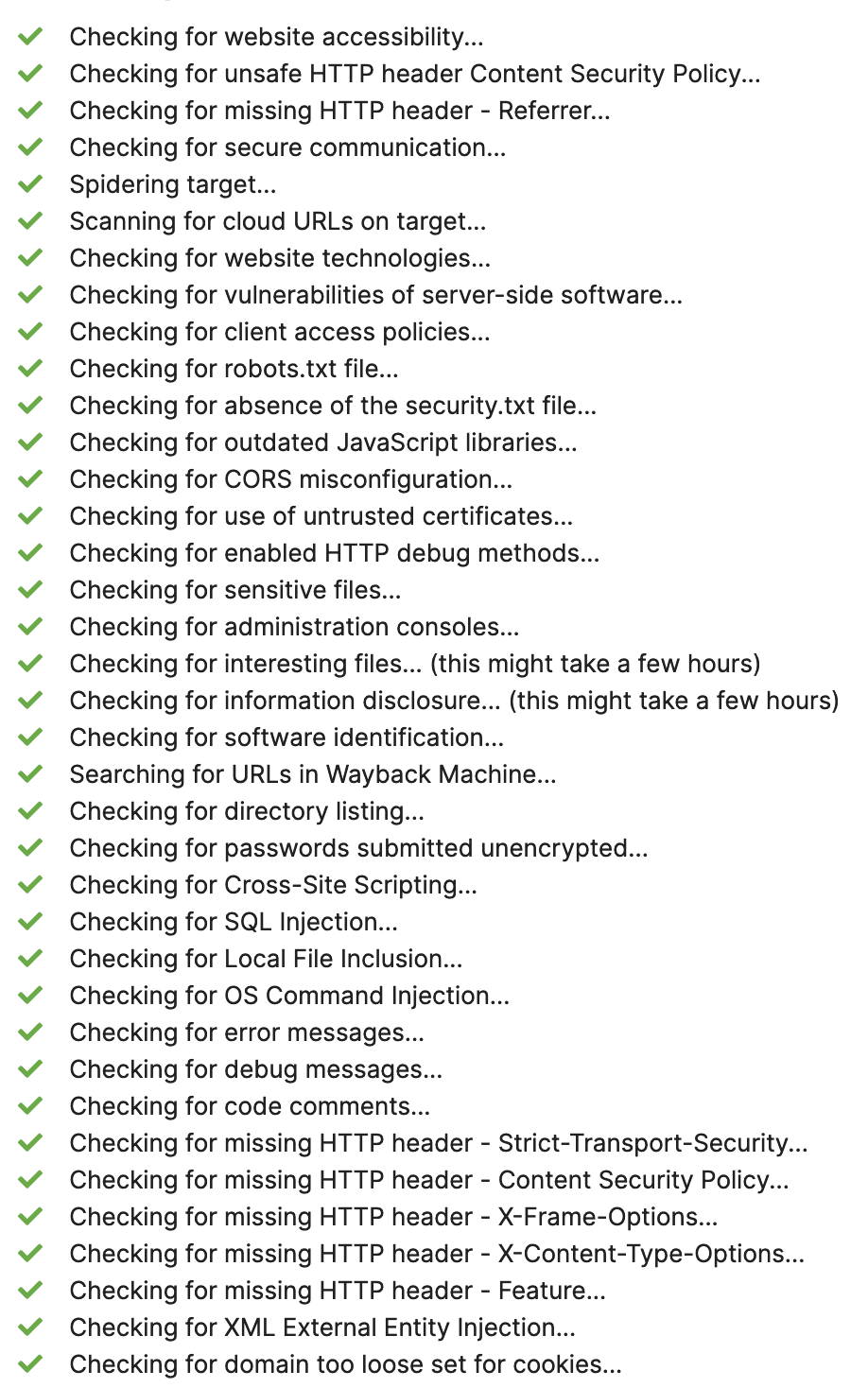
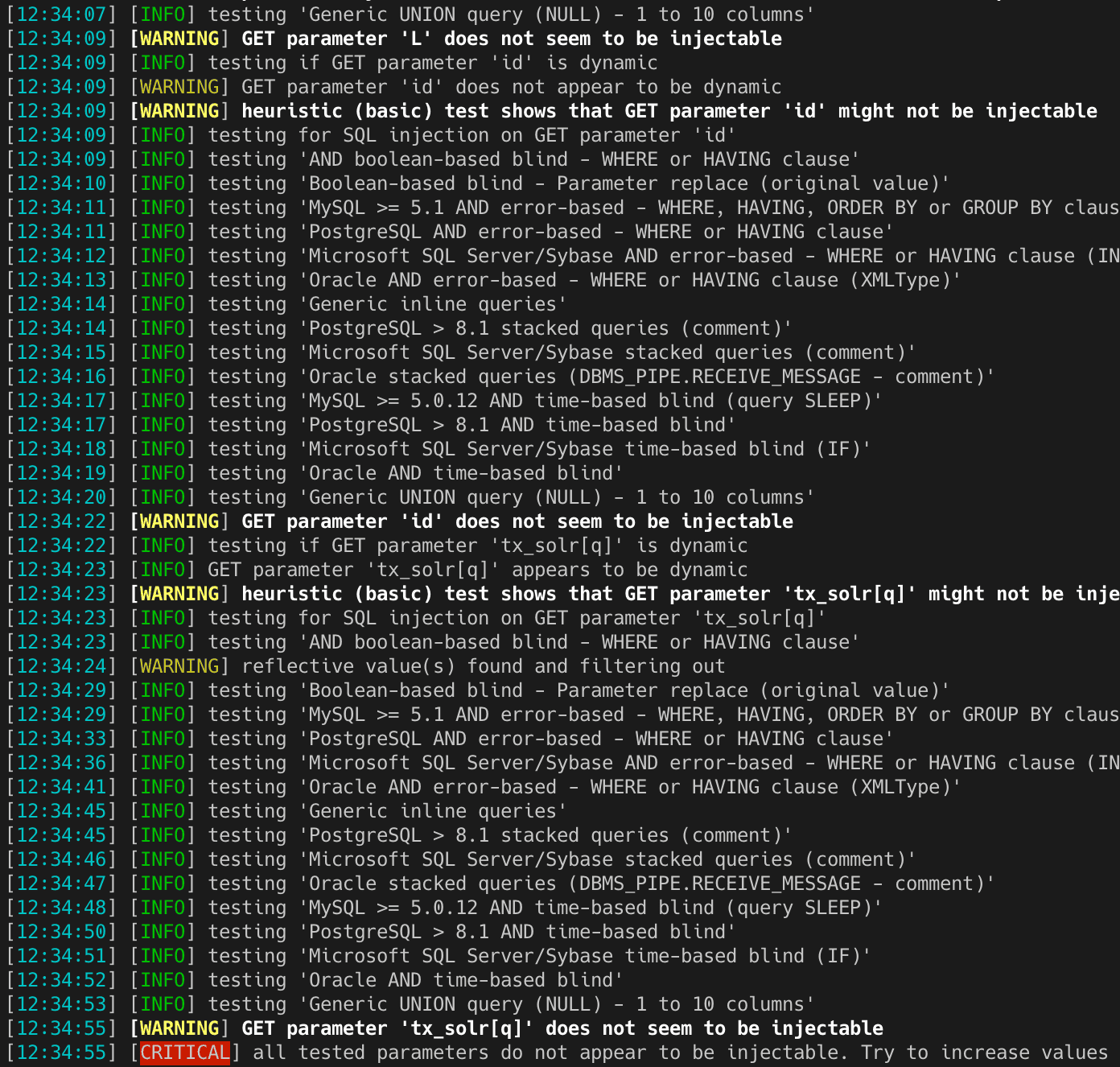
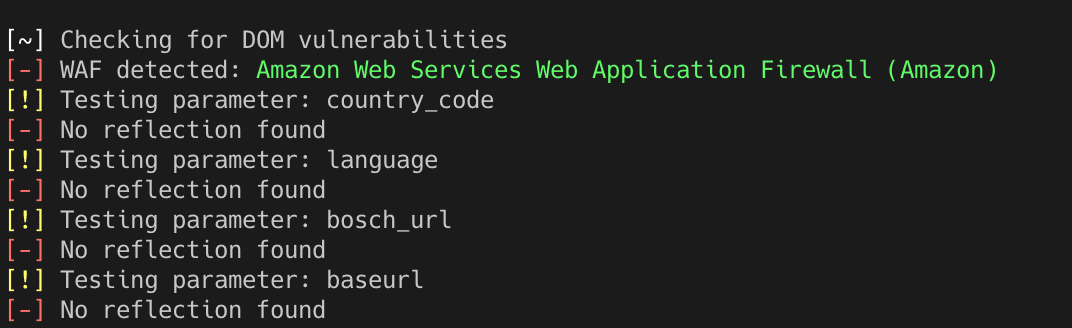
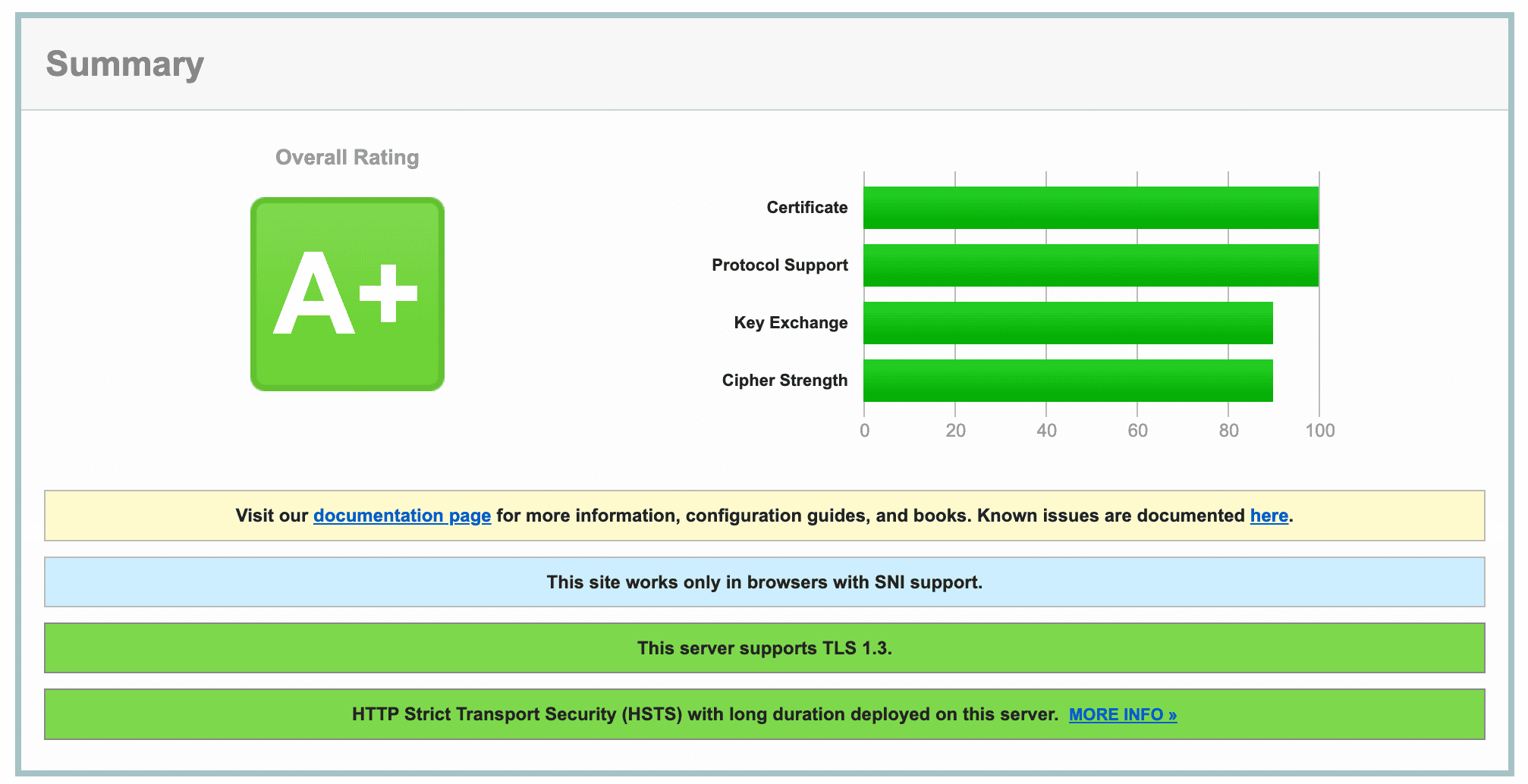
We check your website and your hosting environment for known security problems and configuration errors. Either as a one-off or as a regular service. If we find vulnerabilities or configuration errors, we will help you fix them if necessary.
This offer includes the following components.