Requirements
The installation examples are based on the following environment:
- (Virtual) server with Debian 11, Docker and docker-compose.
- nginx (+ letsencrypt) as reverse proxy for the wg-easy administration interface
wg-easy
Wireguard is already included in many modern Linux kernels and is becoming more and more standard. Compared to solutions like OpenVPN it is fast and needs less resources. There is a large number of configuration options that can be stored in text-based configuration files. To simplify this rather complex configuration, there are various tools such as wireguard-ui or wg-easy.
Setup wg-easy with docker-compose
Once Docker and docker-compose are set up, wg-easy can be started using the following configuration:
version: "3.3" services: wg-easy: environment: # !! Required: # Change this to your host's public address - WG_HOST=some.domain.com # Optional: - PASSWORD=somesecurepassword - WG_ALLOWED_IPS=0.0.0.0/0 #- WG_PORT=51820 #- WG_DEFAULT_ADDRESS=10.8.0.x #- WG_DEFAULT_DNS=4.4.4.4 #- WG_MTU=1420 #- WG_ALLOWED_IPS=192.168.15.0/24, 10.0.1.0/24 #- WG_PRE_UP=echo "Pre Up" > /etc/wireguard/pre-up.txt #- WG_POST_UP=echo "Post Up" > /etc/wireguard/post-up.txt image: weejewel/wg-easy container_name: wg-easy volumes: - .:/etc/wireguard ports: - "51820:51820/udp" - "51821:51821/tcp" #restart: unless-stopped restart: always cap_add: - NET_ADMIN - SYS_MODULE sysctls: - net.ipv4.ip_forward=1 - net.ipv4.conf.all.src_valid_mark=1 logging: options: max-size: "2m" max-file: "20"
The container is then started using docker-compose up -d.
Assuming the correct nginx proxy configuration, the admin interface is now accessible via e.g. https://some.domain.com:
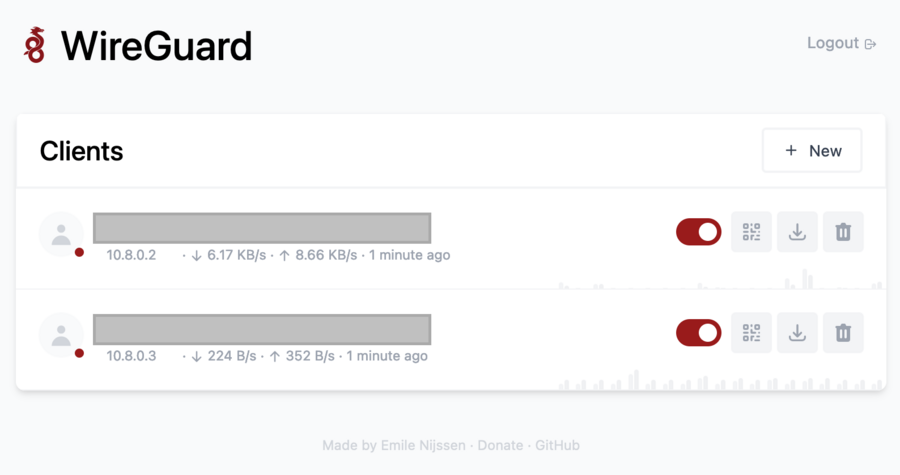
Profiles for individual users can now be created here. The respective configuration can be downloaded and loaded in one of the many Wireguard clients (Windows, Linux, Mac, Android, iOS)(https://www.wireguard.com/install/).
If a client successfully connects to the Wireguard server, all network traffic is routed over this connection. This means that the clients are now on the Internet with the identical static IP of the Wireguard server. This makes it easy to control access to IP-protected resources, for example.
As a further addition, the Wireguard server can be integrated into a (virtual) local network. In this way, particularly sensitive data can be accessed exclusively via this local network and can no longer be accessed via the Internet.
Other
If an external firewall is connected upstream (strongly recommended), port 51820 (UDP) must be enabled on this firewall. Without this, the Wireguard server cannot be reached by the clients.
In addition, it is recommended to allow access to the wg-easy interface only for connected VPN clients and not to make it publicly available on the Internet. Even with a strong password, the risk of unauthorized access is far too high.

